How to Use a Playbook to Add Geographical Data for IP Addresses to a Microsoft Sentinel Incident
Playing with GEO Data
We have a Playbook out on the official GitHub Repo that queries the IP-API.com website with IP addresses and then writes the geographical information to an Incident’s Tags. This is useful, but it’s been found to be too limiting based on the amount of information IP-API returns versus how little data a Tag can hold.
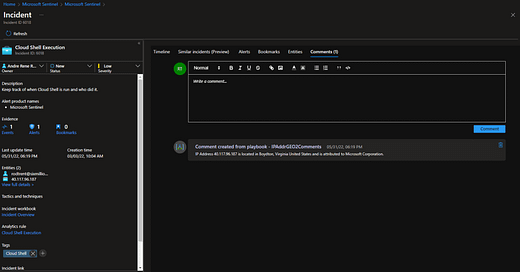
Based on customer request I’ve modified this somewhat so that more information is retrieved and then housed in the Comments section (instead of Tags) of a Microsoft Sentinel Incident. This ensures you can be creative in what data is stored for the Investigation without worrying about being careful about space allotment. Ultimately, the more context you can provide during your investigation research is going to help close Incidents quicker.
Here’s what this looks like:
I’ve placed the new Playbook (with full Deploy to Azure capability) on my own GitHub repo here: https://github.com/rod-trent/SentinelPlaybooks/tree/master/IPAddr2GEO2Comments
Don’t forget to jump through each step to make sure you’ve made the proper connections after deployment.
[Want to discuss this further? Hit me up on Twitter or LinkedIn]
[Subscribe to the RSS feed for this blog]
[Subscribe to the Weekly Microsoft Sentinel Newsletter]
[Subscribe to the Weekly Microsoft Defender Newsletter]
[Learn KQL with the Must Learn KQL series and book]