Periodically, customers will ask to be able to review the list of Microsoft Sentinel detection rules (Analytics Rules) with the associated MITRE ATT&CK tactics. This is a good ask.
Before I jump directly into uncovering a relatively unknown option for viewing this data, I think it will help to expose those options that are more readily known.
There are a few known ways to get this information.
MITRE ATT&CK Workbook
The first is through the MITRE ATT&CK Workbook supplied in the Microsoft Sentinel console.
This Workbook supplies various visual views of the tactic coverage available in Microsoft Sentinel.
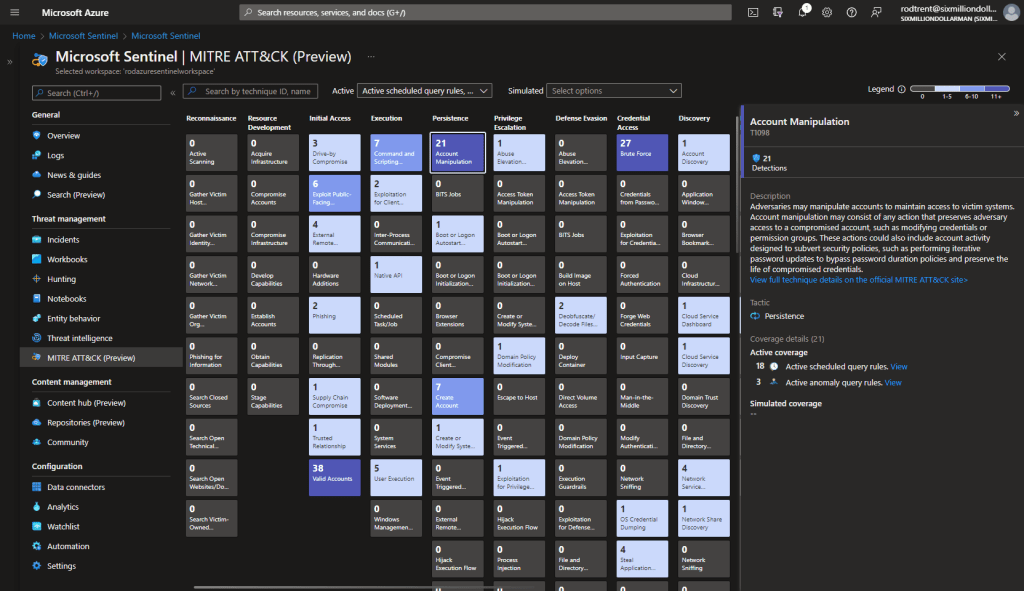
MITRE ATT&CK Blade
Another obvious way to accomplish this is using the MITRE ATT&CK blade in the Microsoft Sentinel console.
This option provides an awesome way to view current MITRE coverage and identify gaps and simulate possible coverage with available detections.
See the following for more information about this feature: Understand security coverage by the MITRE ATT&CK® framework
Threat Analysis & Response Solution
In the Microsoft Sentinel Content Hub, there’s a couple Workbooks that can be deployed through deploying the Threat Analysis & Response solution.
These Workbooks enable you to view the current environment coverage dynamically using the power of Azure Monitor capabilities.
Sentinel REST API
Another known, but often overlooked, option is through using the Microsoft Sentinel REST API.
The REST API for Alert Rule Templates – List Definition enables you to retrieve all the existing detection rules. Both Scheduled and Fusion rules have a properties.tactics string that contains the tactics names. You can choose to generate the entire list or pare down the list to just show the rule name and the associated tactics.
If this interests you, see: Alert Rule Templates – List
Viewing the List Directly in Excel
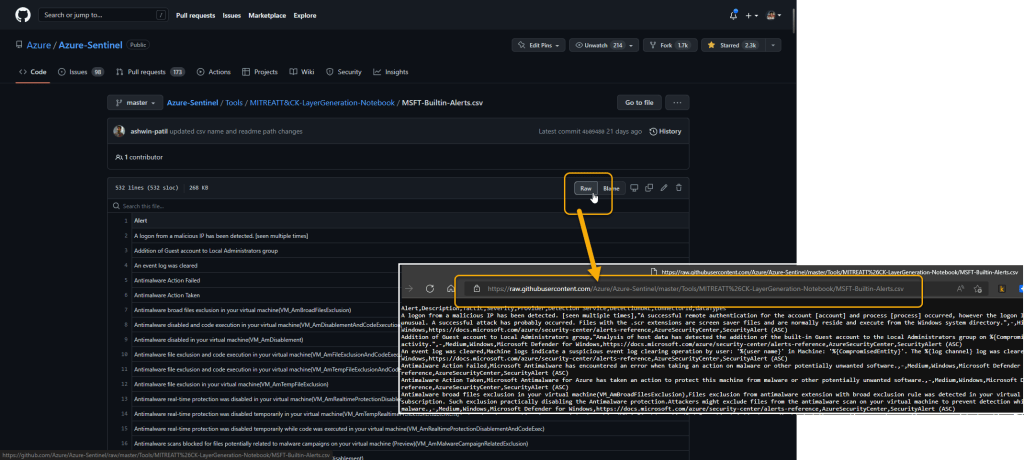
For this lesser-known trick, I’ll use the first known option I covered (the MITRE ATT&CK Workbook) as the source. Unless you’ve dug through the Workbook and looked at the code you won’t realize that this Workbook actually gets some of its data from a .csv file sitting on the Microsoft Sentinel GitHub repository.
There’s a file called MSFT-Builtin-Alerts.csv that sits at Azure-Sentinel/MSFT-Builtin-Alerts.csv at master · Azure/Azure-Sentinel (github.com). The Workbook calls this file for the MITRE ATT&CK data that it displays.
But we can use this curated file ourselves.
To pull the data into Excel, do this:
[1] Jump out to the file location (https://cda.ms/4rx), open the RAW version of the file, and grab the RAW link.
If you don’t want the hassle of doing step 1 yourself, just use this link: https://raw.githubusercontent.com/Azure/Azure-Sentinel/master/Tools/MITREATT%26CK-LayerGeneration-Notebook/MSFT-Builtin-Alerts.csv
[2] Open Microsoft Excel, choose the Data tab to import a text/CSV file, and paste the file link into the file source to open it.
[3] When prompted, you only need to choose the Load option as shown in the next image.
Once the data is loaded you can use the power of Microsoft Excel to shift and filter the data any way you want.
[Want to discuss this further? Hit me up on Twitter or LinkedIn]
[Subscribe to the RSS feed for this blog]
[Subscribe to the Weekly Microsoft Sentinel Newsletter]
[Subscribe to the Weekly Microsoft Defender Newsletter]
[Learn KQL with the Must Learn KQL series and book]